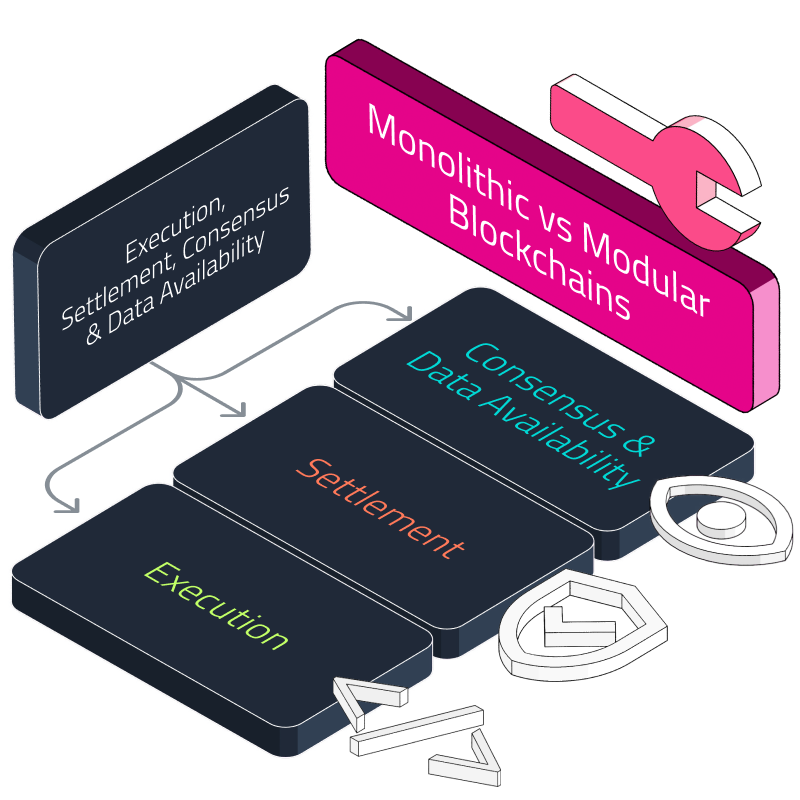
Modular blockchains represent the next evolution in decentralized technology, enabling unprecedented scalability, interoperability, and flexibility. Builders have an exciting opportunity to propel this ecosystem forward by creating innovative applications, platforms, and tooling. This guide will provide developers with actionable knowledge to build on modular blockchains effectively.
Modular designs allow for an unprecedented level of flexibility and customization. Developers can tweak consensus mechanisms, add support for smart contracts, enable cross-chain interoperability, and integrate various features and functionalities. The result is a vibrant ecosystem of tailored blockchains built using modular toolkits.
The following sections will explore the techniques and components of engineering modular blockchains. We'll explore the fundamentals, infrastructure, smart contracts, consensus, security, deployment strategies, and risk mitigation. This guide aims to equip developers with the knowledge to start building the decentralized systems of the future.
Infrastructure and Tooling
Modular blockchains require a robust infrastructure and developer tooling to enable rapid innovation. Here is a guide to the key components:
Modular Runtimes
The modular runtime sits between the blockchain protocol and the application layer, allowing developers to mix and match components. Popular modular runtimes include Cosmos SDK, Polkadot Runtime Environment (PRE), and Substrate. These provide core functionality like accounts, staking, governance, and upgrades out-of-the-box.
Interoperability Bridges
Bridges allow modular blockchains to connect to external networks like Ethereum. They facilitate cross-chain transfers of assets and data. Leading bridge technologies include Inter-Blockchain Communication (IBC), Polkadot Relay Chain, various peg zones on Cosmos, Atomic swaps, and sidechains like Avalange Bridge.
Node Clients
Node clients run the blockchain software and validate transactions. Modular node clients like Tendermint, Parity, and Substrate provide flexibility to customize consensus and other parameters. On Ethereum, the nodes and clients are divided into two - the execution and consensus clients- and there are several of them from which to choose.
Simplified diagram of a coupled execution and consensus client. Source: Ethereum docs.
Developer Tools
Developer tools like languages (Rust, Go, and JavaScript), SDKs, and IDEs optimize and simplify app development. Rust, Golang, and TypeScript are languages commonly used for modular blockchains. SDKs like Covalent SDK, CosmJS, and Polkadot.js provide easy integration.
The popular IDEs used are Remix IDE, which is browser-based, focused on Ethereum and Solidity development, and offers debugging capabilities, IntelliJ - JetBrains IDE with Rust, Go, JavaScript support, and plugins, and Visual Studio Code - with extensions like rust-analyzer offer support for blockchain languages.
Other Tools
Truffle: Development environment and asset pipeline for blockchains using EVM.
Ganache: Personal Ethereum blockchain for testing.
Lity: Language for writing chain specification scripts when using Substrate.
The modular stack opens up endless possibilities for experimentation and customization. Blockchain developers can boost their efficiency in creating innovative modular solutions using these infrastructure elements and development tools.
Interoperability and Cross-Chain Communication
Blockchain interoperability refers to the capacity of different blockchain systems to exchange data, messages, and digital assets. Interoperability between various blockchains is crucial in enabling modular architectures. There are a few core protocols that facilitate communication and interaction between separate chains:
Inter-Blockchain Communication (IBC) Protocol: The IBC protocol defines a standard interface for blockchains to connect. It handles authentication, ordering, and data transfer between chains, allowing heterogeneous blockchains to transact and exchange value. Capabilities enabled by IBC:
Cross-chain transactions between arbitrary blockchains.
Transfer of tokens and other digital assets across chains.
Communication of arbitrary data between blockchains.
Multi-hop transactions spanning multiple chains.
Hashed Timelock Contracts (HTLC): These smart contracts facilitate swaps between assets on blockchains without a trusted intermediary. The assets are locked up and released when the corresponding asset is sent from the other chain. Atomic swaps are enabled by HTLC, which acts as a virtual vault or a cryptographic escrow account that only executes when the correct amount of tokens has been deposited into the contract.
Commitment Schemes: Commitment schemes allow data to be committed to one chain and later revealed on another. This links activities between chains and enables new types of cross-chain applications.
Building with Interoperability in Mind
Adopting these technologies necessitates shifting your perspective from a single-chain mindset to a more integrated approach. Here are a few examples of how to build with interoperability as a central focus:
Use interoperability protocols like IBC to transfer data and value between modular blockchain components.
Leverage standardized data formats like IPLD and canonical data models for interoperability.
Design modular and extensible codebases that integrate external modules and data sources.
Utilize cross-platform development languages and frameworks where possible.
Implement platform-agnostic APIs and middleware layers for easy integration. Covalent is the leading provider of indexed blockchain data, covering over 200 blockchains. These middleware layers provide easy access to infrastructures your app may need.
Plan for multi-chain architectures and decentralized data storage from the start.
To maximize compatibility, adopt common standards and specifications like ERC-20, ERC-721, ERC-1155, and ENS.
Below is a list of common ERC standard tokens used across EVM chains.
Cross-Chain Communication
Enabling seamless communication and interaction between blockchains is critical for realizing the full potential of modular blockchain architecture. Cross-chain technology refers to the ability to transfer data and tokens between different blockchains. This section provides a technical walkthrough for facilitating cross-chain asset and data transfer.
How Cross-Chain Communication Works
At a high level, cross-chain communication involves building a bridge between two or more blockchains and facilitates the transfer of assets and data between them. This bridge acts as an intermediary that locks the assets on the source chain and mints equivalent representations of those assets on the destination chain.
Components of cross-chain bridges include:
Relayers: These nodes listen for events on one chain and relay the information to another through signed transactions. They facilitate communication between chains.
Validators: Nodes that are responsible for validating the proofs and signatures submitted by the relayers. They prevent fraudulent transactions or activities.
Consensus mechanisms: Cross-chain bridges have consensus mechanisms for approving asset transfers. Common ones include proof-of-stake and byzantine fault tolerance.
Smart contracts: Smart contracts lock and unlock assets on each chain during transfers. They also define the logic around minting wrapped assets.
Security: Cryptographic proofs like Merkle proofs provide legitimacy and finality around cross-chain transactions.
Optimizing Cross-Chain Bridges
Several optimization strategies can improve the efficiency and security of cross-chain bridges:
Sharded relayers: Relayers can be partitioned into shards for parallel processing of transactions.
Interoperability standards: Common standards like W3C's Interledger Protocol and Chainlink’s cross chain interoperability protocol (CCIP) can simplify cross-chain interoperation.
Hierarchical bridging: Chains can be bridged through a central hub rather than individual bridges between each pair.
Economic incentives: Well-designed token economic incentives can attract reliable relayers and validators to operate the bridge.
The illustration below shows the communication between smart contracts across multiple blockchain networks using Chainlink’s CCIP.
Source: Chainlink.
Optimizing Smart Contract Development for Modular Blockchain Ecosystems
Smart contracts are self-executing programs stored on the blockchain that run when predetermined conditions are met. They are a foundational component of blockchain platforms and enable a wide range of decentralized applications.
They are a vital component of modular blockchains, enabling complex logic to be executed in a decentralized manner. Since each module is separated, each smart contract could function independently, allowing developers to create and manage smart contracts in isolation, reducing complexities and dependencies.
Considerations for Smart Contract Design
Smart contracts take on new possibilities and challenges in a modular blockchain architecture. Since each module or component of a modular blockchain focuses on a specific functionality, smart contracts must be designed with interoperability and communication between modules in mind.
Important considerations include:
Chain-specific optimization: Smart contracts can be tailored to run optimally on application-specific chains rather than a generalized environment. This approach improves efficiency and reduces bloat.
Segregated security: Sensitive smart contracts can be deployed on specialized security-focused chains while minimizing the computational load on the core chain.
Oracles: Oracle services provide external data to smart contracts outside the blockchain, allowing smart contracts in one module to leverage data from other modules or external systems.
Digital Asset Abstraction: Abstracting digital asset logic from smart contract business logic to increase flexibility. Asset-related logic can be maintained separately from the core business rules.
Inter-Contract Communication: Mechanisms like dispatchers allow smart contracts in different modules to call one another while maintaining separation of concerns. This type of communication enables complex cross-module workflows.
Upgradeable Contracts: Proxies and registries can upgrade smart contracts, avoiding redeploying contracts when required changes are especially useful in modular systems.
These alterations allow for smart contracts that are more flexible, optimized, and communicative across modular architectures. Developers building on modular platforms must consider the multi-chain environment when designing their smart contract logic and interactions.
Approaches for Building and Deploying Smart Contracts
Let’s explore some recommended approaches for building and deploying smart contracts:
High-level language: Write contract logic in a high-level language like Solidity, allowing easy debugging and iteration. Lower-level languages can optimize gas costs but reduce readability.
Modular frameworks: Modular frameworks may have multiple virtual machines and execution environments. Understand where you will deploy your contract and test accordingly.
Reuse contracts: Reuse already audited and community-vetted contracts when possible instead of coding contracts from scratch.
Single responsibility contracts: Break complex contract logic into minor reusable contracts focusing on single responsibilities, which improves security and makes iterative upgrades easier.
Input/output validation: Ensure proper validation of all inputs and outputs to prevent unexpected behavior. Guard against reentrancy attacks.
Transaction ordering: Transaction ordering and finality are essential for contract interactions across chains. Understand timing guarantees.
Portable interfaces: Applications can be built by combining multiple contracts from various specialized chains. Keep contract interfaces portable.
Automated testing: Test end-to-end functionality thoroughly across chains, shards, and layers. Automated integration testing is highly recommended.
Navigating Consensus Mechanisms in Modular Blockchains
When it comes to modular blockchains, the ingenuity lies not just in their flexibility of design but also in the way consensus can be crafted to cater to diverse application needs. Developers leveraging these platforms know that the consensus technologies integral to modular systems set them apart from conventional monolithic structures. Therefore, the emphasis should be on practical guidelines and innovative solutions that effectively utilize these technologies for scalable dApp development.
Practical Guidelines for Consensus in Modular Blockchains
Understand Module-Specific Consensus Needs: Analyze the requirements of your DApp's module. High-speed microtransactions demand faster consensus mechanisms, while a module requiring immutable records might necessitate a more robust and slower consensus.
Leverage Framework Flexibility: Use the modular blockchain framework to experiment with consensus algorithms that best suit your module's purpose. This could mean starting with a Proof of Authority (PoA) consensus for rapid iteration during development before transitioning to a Proof of Stake (PoS) mechanism for better decentralization in production.
Utilize Consensus As a Service (CaaS): Consensus-as-a-Service can be intricate but provides an abstraction layer that allows developers to focus more on application logic than the underlying consensus mechanics. It is a cloud-based service that helps developers to deploy and manage consensus mechanisms. Some popular CaaS providers are Blockdaemon, Kaleido, etc.
Ensure Security is not Compromised: Multiple modules increase the surface area for potential attacks. Use layered security measures that protect individual modules without compromising the consensus efficiency across the network.
Consideration for Governance: Implement on-chain governance modules that provide a way to manage consensus parameters and updates democratically, ensuring the network adapts to changing requirements over time.
Strategies & Considerations for Developers
Design for Future Flexibility: Your blockchain's modular nature means you don't have to get everything perfect from the get-go. You can swap different components, including consensus mechanisms, to meet the changing needs of your users or the technological landscape. Consider future-proof design on the application layer that considers potential consensus upgrades or changes.
Rethink Traditional Trade-offs: Traditionally, blockchains have needed to balance decentralization, security, and scalability, often sacrificing one for the other two. With modular blockchains, you have an opportunity to readdress these trade-offs. For instance, consensus mechanisms guaranteeing high transaction speeds can be used for specific modules that require them, while others could use more secure consensus mechanisms.
Planning for Consensus Failures: While we focus on optimizing consensus mechanisms, it is also wise to consider the potential for consensus failure. Design redundancies and implement safeguards against network splits (forks), reptilian attacks, selfish-mining attacks, or other exploits that could threaten consensus integrity.
Security Measures and Considerations
Modular architectures introduce unique security challenges that developers must address to build robust blockchain applications. Because modular blockchains break up components into separate modules, this expands the potential attack surface, making each module a possible target for exploits. Developers should take care to mitigate risks at each layer of the stack.
Unique security considerations in modular blockchain environments include:
Interoperability threats: Interconnecting multiple chains creates potential attack vectors where vulnerabilities in one chain may impact others. Developers should implement strict verification procedures for cross-chain communications.
Increased complexity: The potential for bugs and exploits increases with each additional module and connection. Subtle bugs can emerge from the intricate messaging and data flow between components. Rigorous testing and formal verification are necessary to identify edge cases that could be exploited.
New points of centralization: Modules like sidechains often rely on validators to bridge to mainchains. Centralized components can be single points of failure. Distribute control and leverage game theory incentives.
Smart contract interactions: Contract logic must account for cross-chain implications. Ensure proper handling of asset transfers between chains.
Fork management: Forks may propagate in unexpected ways across chains. Plan fork handling carefully in modular environments,
Upgradability: Plan smart contract and module upgrades carefully to avoid chain disruptions. Make upgrades atomic when possible.
Module security: Treat each module, such as sidechains, as its blockchain with individual security needs. Don't assume all chains share the same properties.
Bridge Threats: Securing the bridges or relays that connect modules and chains is another major challenge. Attackers may target bridge contracts to steal funds, freeze transfers, or cause denial of service. Strategies like using decentralized networks of relayers, over-collateralization, and monitoring for suspicious activity can help mitigate bridge-based attacks.
Consensus Management: Integrating different consensus mechanisms at the consensus layer creates new attack vectors, like double spending across chains with varying finality guarantees. Developers must synchronize the state across components by utilizing different consensus models properly.
Sybil attacks: On public modular blockchains, governance mechanisms that rely on voting could also be manipulated by attackers obtaining disproportionate voting power through Sybil attacks and other techniques. A robust governance model resistant to various influence tactics is critical.
Deployment and Continuous Integration
Deploying modular blockchain components requires thoughtful strategies around testing, updating, and overall software development lifecycles. Robust and continuous practices are crucial to ensuring scalability.
Testing Strategies
Thorough testing is critical before deploying any blockchain component. Given the immutable nature of blockchain data, bugs or vulnerabilities could have permanent consequences. Developers should implement unit tests, integration tests, and end-to-end tests using frameworks like Truffle or Hardhat. Tests should cover functionality, security, gas costs, and performance.
Modular architectures allow developers to test components in isolation before integrating them. Isolating consensus mechanisms, data availability layers, execution engines, and smart contracts enable targeted testing. Mocking services and simulating interactions are also essential techniques.
Deployment Strategies
Modular design enables incremental deployment of individual components. Developers can deploy consensus mechanisms first, then data availability layers, and finally, application layers. This staging allows testing at each level.
Upgradability is also critical for production deployments. Developers should architect contracts and ecosystems for easy upgrades, configurations, and maintenance. Upgradeable proxies and delegated logic patterns are helpful.
Updating Strategies
Once in production, bug fixes and improvements will require updating deployed code. Developers should plan processes for migration and versioning. Techniques like proxy contracts, zero-downtime registries, and live switching minimize disruption.
For major updates such as protocol changes, gradual, staged rollouts may be necessary. Strategies like on-chain governance and fork-based upgrades can transition networks smoothly.
Identifying and Mitigating Risks
Modular blockchain development comes with its own unique set of risks that developers need to be aware of. Here are some of the most common pitfalls and how to avoid them:
Poor Validation of Inputs and Outputs
One of the most significant risks is failing to validate inputs and outputs between modules or chains properly. For example, if a smart contract on Chain A is calling a smart contract on Chain B, it needs to thoroughly validate the response from Chain B before executing. Not doing proper validation can lead to unexpected behavior or exploits.
To mitigate this, always double-check validation logic when passing data between different components. Use well-tested libraries and schemas whenever possible.
Inconsistent Error Handling
When connecting various modules, ensure error handling is consistent across the entire architecture. For example, if the consensus module throws a specific error, other modules interacting with it should handle it properly.
Having inconsistent error handling can lead to failures cascading through the system. Define comprehensive error codes and types to share across modules. Document expected errors and make error handling a priority.
Poor Access Controls
Access controls and permissions need special attention in modular environments. Review the access controls between smart contracts, APIs, networks, and modules. Verify that assets, data, and functionality are only accessible to authorized entities.
Use well-vetted authentication mechanisms like OAuth 2.0. Implement access control lists and role-based permissions where applicable.
Comprehensive Monitoring and Security Between Modules
For a modular blockchain to function seamlessly, comprehensive monitoring, alongside diligent examination of inter-module connections, is vital. Implement robust tools for monitoring, including logging, metrics, and analytics capacities across all modules and chains, with alerts set for critical issues. Prioritize traceability between chains and transactions. Additionally, conduct threat modeling and risk analysis to identify potential vulnerabilities between modules. Ensure redundancy for critical connections and adhere to cybersecurity standards to fortify interfaces and valid data passing between modules.
Conclusion
The potential of modular blockchains to transform and democratize technology is fascinating. As developers, we can actively participate in this movement by building, innovating, and pushing the boundaries of what is possible. If we can dream it, we can code it - the only limit is our imagination.
Contributing to open-source modular blockchain projects leads us closer to an equitable and transparent future. The applications we create today on these modern frameworks can solve real-world problems and empower people everywhere. We get to be at the forefront, shaping the next generation of the internet - founded on decentralization, security, and community collaboration.